While the rest of the Plasma team is sprinting in Germany, I’m unfortunately tied down to my chair at home and trying to sprint as well.
Backends
The main work I’ve been doing since I announced Plasma Vaults was to refactor the hell out of the Vaults infrastructure to allow me to support more encryption engines.
I’ll blog about some of the more fun parts of this refactor later.
The main reason why I am mentioning this now is that we now have two different choices for Vault encryption.
The first is (as previously mentioned) EncFS, and the newly added one is the young but promissing CryFS.

CryFS is a more modern system that tries not to repeat the same errors that EncFS (and eCryptFs) have. It does not expose the number of files, directory organization, nor sizes of the files stored in the system, while not having any significant known drawbacks.
One thing that I’d like to say here is that the important word in the above sentence is known.
It is true that EncFS has known security issues thanks to the independent security audit by Taylor Hornby, so you know that it is not safe in certain use-cases.
But its huge advantage is that you know what its problems are. For the newer systems like CryFS, there is no known independent security audits (if you find one, please notify me).
This means that, at this point, the choice is between a known system with known faults that you will most likely be safe with if you use it correctly, and a new system that does not have those faults, but its faults are unknown.
I’m investigating a few systems more (including eCryptFs), but I’ll write about them when they get supported by Plasma Vaults.
A bit on the UI
I’ve also been polishing the UI a bit.
Instead of having a huge dialogue, the vault creation is now in a nice-looking wizard. I’m not a fan of wizards, but in this case it is a much better choice.
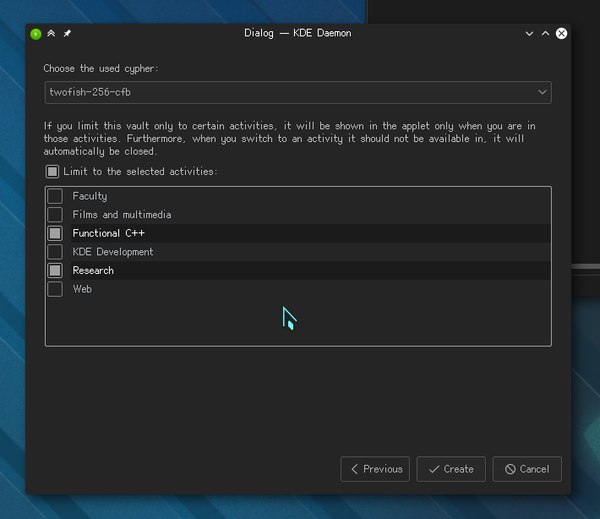
Apart from not looking as cluttered as the previous one, it also allows different backends to have different options (like choosing the cypher in CryFS).
Fun with icons
Alex has made a few nice icons for this, and now I’m experimenting how can I use them to improve the user experience.
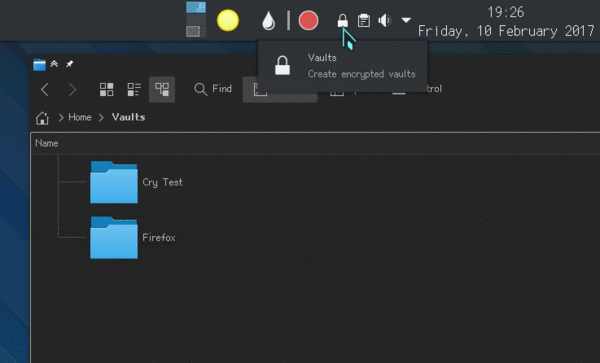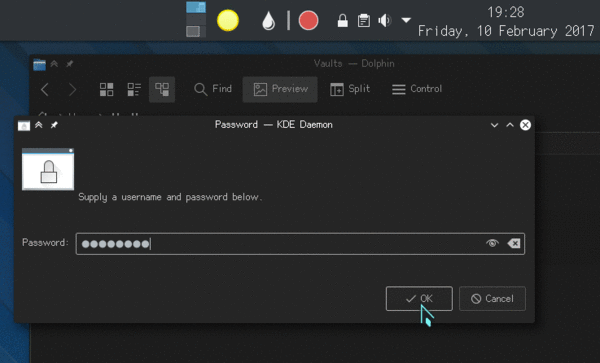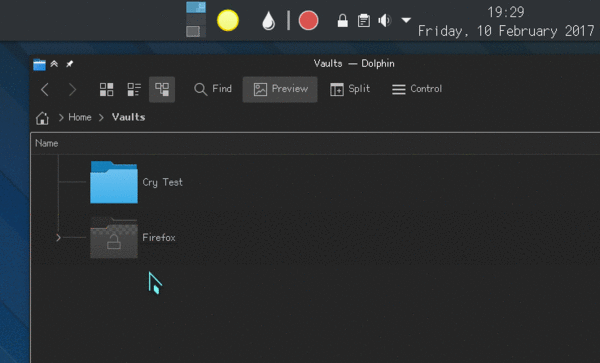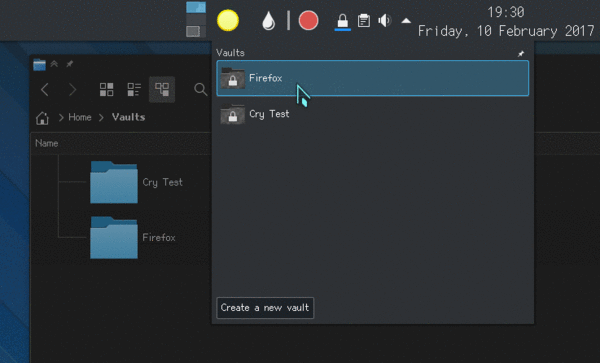
One of the things I’m trying out is to set the default icon for the vault folder, so that, when you open the Vault, its folder’s icon changes to notify you that that its contents is encrypted.




